In the world of cryptocurrencies, security is paramount. Unlike traditional bank accounts, crypto assets are self-custodied—meaning you, and only you, control your funds. That control starts with your Trezor hardware wallet and the secure way you access it through Trezor login. Whether you’re a first-time crypto user or a seasoned investor, understanding how to safely log in and manage your Trezor wallet is essential.
This guide walks you through everything you need to know about Trezor login—from setup to best practices for security.
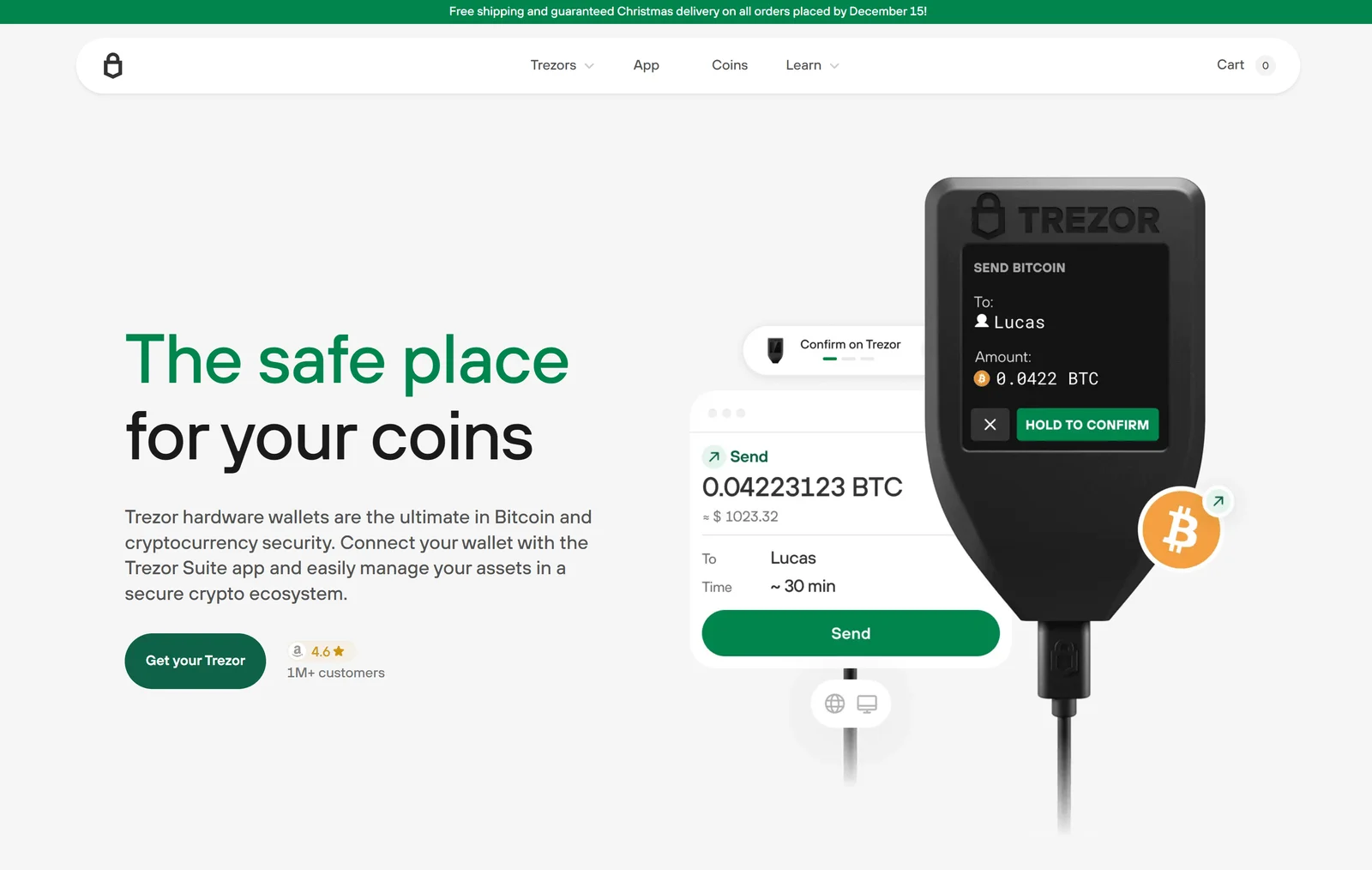
Trezor login is the process of accessing your Trezor wallet through Trezor Suite or compatible web interfaces. Unlike online wallets that store your private keys on a server, Trezor keeps your keys offline on the device itself. This means logging in isn’t just entering a password—it involves securely connecting your device and confirming actions directly on it.
With Trezor login, you can:
Trezor login is the gateway to complete ownership and control over your crypto.
Your private keys are the keys to your crypto kingdom. Anyone with access to your private keys can control your funds. Trezor login ensures that:
Simply put, Trezor login is not just about convenience—it’s a critical layer of security that keeps your crypto safe.
Logging in to your Trezor wallet is straightforward, but it’s important to follow the correct steps for maximum security.
Trezor Suite is the official software interface for managing your Trezor wallet. It’s available for:
Always download Trezor Suite from the official Trezor website to avoid phishing or malicious software. Once installed, open Trezor Suite to begin the login process.
Use the USB cable provided with your Trezor device to connect it to your computer or mobile device. Make sure your device is physically present—you’ll need it for authentication.
Your Trezor device is protected by a PIN code. Enter the PIN directly on the device using the randomized on-screen keypad. This protects against keyloggers and unauthorized access, even if your computer is compromised.
Once the device is connected and the PIN is entered, Trezor Suite will recognize your wallet. If it’s your first time logging in, you may need to:
After authentication, you can access your dashboard, manage your crypto, and perform transactions securely.
Trezor supports hundreds of cryptocurrencies. After logging in, you can add accounts for the coins you want to manage. Each account allows you to monitor balances, send and receive funds, and track transaction history—all with device verification for security.
Security doesn’t stop at connecting your device. Follow these best practices to keep your crypto safe:
By following these steps, you can ensure that your Trezor login and wallet remain fully secure.
Since 2014, Trezor has been a pioneer in hardware wallet security. Its open-source design allows independent security audits, providing transparency and trust. Millions of users worldwide rely on Trezor to protect their crypto assets, from Bitcoin and Ethereum to a wide range of altcoins.
Trezor login ensures you remain the sole owner of your private keys, giving you total control over your financial future. It’s not just about storing crypto—it’s about safe, accessible, and confident ownership.
Logging in to Trezor is the first step toward taking full control of your crypto. Once connected, you can:
Visit the official Trezor website to download Trezor Suite and securely log in to your wallet today. With Trezor login, your crypto remains secure, accessible, and completely under your control.